各位彦祖,求教下nat的问题。
情况是酱紫的。
局域网有一个debian(192.168.50.110),用tproxy代理局域网以及debian本机自己的流量。
主路由器用的ccr1009进行IP分流,局域网设备使用无问题,但是路由器本机流量就不行,除非snat上来一条下面红色那个才行。。。
[admin@ccr1009] >/tool fetch mode=http url="https://www.google.com.hk/images/branding/googlelogo/2x/googlelogo_color_92x30dp.png"
status: finished
downloaded: 3KiBC-z pause]
total: 3KiB
duration: 0s
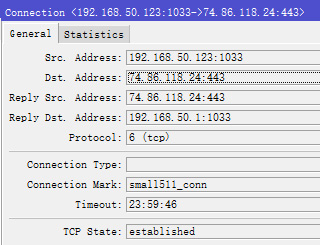
但是加上去之后,部分连接显示的reply dst address就是会网关
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
# aug/19/2020 16:33:06 by RouterOS 6.45.9
# model = CCR1009-7G-1C
/ip firewall nat
add action=accept chain=srcnat comment="Accept IPSEC nat" protocol=udp \
src-port=500,4500
add action=accept chain=srcnat comment=\
"defconf: accept all that matches IPSec policy" ipsec-policy=out,ipsec
add action=src-nat chain=srcnat comment="SNAT_plan_B: LAN IP to PPOEOUT SNAT" \
ipsec-policy=out,none out-interface=pppoe-out1 src-address=\
192.168.50.0/24 to-addresses=114.244.160.128
add action=src-nat chain=srcnat comment="SNAT_plan_B: defaut ppoeout snat" \
ipsec-policy=out,none out-interface=pppoe-out1 to-addresses=\
114.244.160.128
add action=masquerade chain=srcnat comment=l2tppool src-address=\
192.168.50.200-192.168.50.249
add action=masquerade chain=srcnat comment="default: masquerabe" \dst-address-type=!local out-interface-list="!WAN Interfaces"add action=dst-nat chain=dstnat comment="Port forwarding: DSM HTTPS" \
dst-address=!192.168.50.0/24 dst-address-type=local dst-port=5001 \
protocol=tcp to-addresses=192.168.50.139 to-ports=5001
add action=accept chain=dstnat comment="Accept Gateway's DNS Request" \
dst-port=53 protocol=udp src-address=192.168.50.110
add action=dst-nat chain=dstnat comment=\
"L7 VIP domain's DNS request Hijacking to Mirotik(UDP)" dst-port=53 \
packet-mark=to1111dns protocol=udp src-address=!192.168.50.110 \
src-address-list=LAN to-addresses=1.1.1.1 to-ports=53
add action=redirect chain=dstnat comment="dns hijacking to Mikrotik UDP" \
dst-address=!192.168.50.1 dst-address-type=!local dst-port=53 protocol=\
udp src-address=192.168.50.0/24 src-address-type=local to-ports=53
add action=redirect chain=dstnat comment="dns hijacking to Mikrotik TCP" \
dst-address=!192.168.50.1 dst-address-type=!local dst-port=53 protocol=\
tcp src-address=192.168.50.0/24 src-address-type=local to-ports=53
